
10 Types of Security Software
Websites, nowadays, are considered the virtual face of any company,and as everyone tries to make the best first impression upon every encounterwith someone new, websites are the same, as they must be pleasantand engaging to impress and capturethe visitors’ attention in a way that leads theminto exploring the pages and the services provided on the platform. However, it doesn’t only revolve around the outer look,websites also must always remain secure as cyber threats continue to evolve.
Content
- Why Software Security is Important
- Software Types Your Business Website Must Have
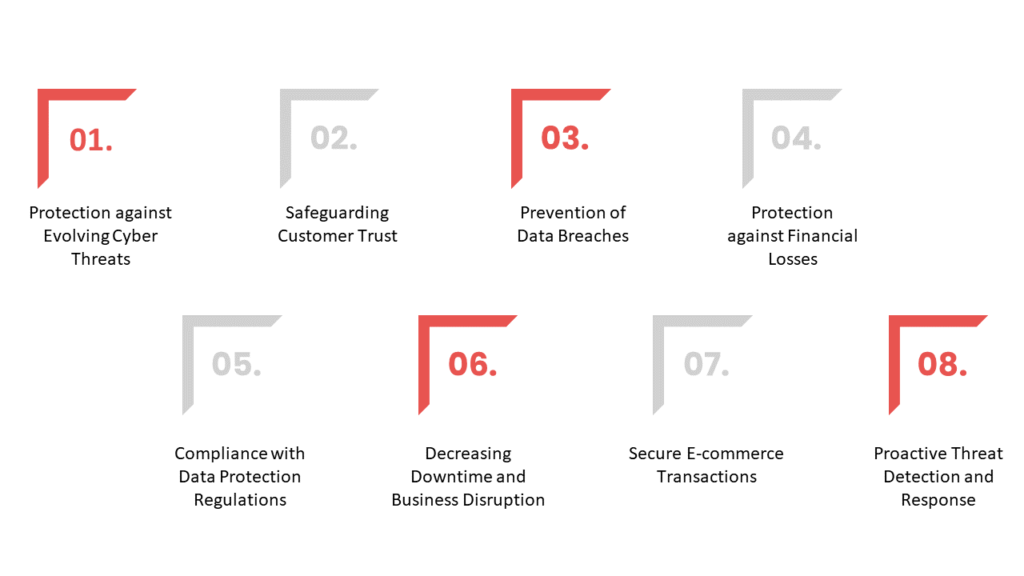
1. Why Security Software is Important
Security Software is important for many reasons:
2. Software Types Your Business Website Must Have
In light of the ceaseless cyber threats, the tools and software used to protect and defend the security of websites are vast and their development is a never-ending process. Below are 10 types of security software, each with different functionality and serving different purposes.
- Antivirus Software:
Antivirus software programs are used to scan and prevent viruses, Trojans, and many other software threats. Such programs will help prevent malware from destroying systems.
- Firewall Software:
Firewall is software that can be installed on hardware and software. It uses predefined security rules to track and control the data transferred through the network. Firewalls are considered the defending wall between a computer or network and potential external threats.
- Encryption Software:
Encryption software works on converting the stored data or even the data in transit from readable to unreadable format. This protects the data from being breached with one more layer that only allows authorized access.
- Intrusion Detection Systems (IDS):
IDS is a network security technology that helps detect unauthorized access, abnormal activities, and potential threats. This type of technology helps in early detection of threats since it works on analyzing patterns and identifying abnormalities.
- Virtual Private Network (VPN) Software:
Virtual Private Network or as it is widely known – VPN is the kind of software that is mainly associated with online privacy. VPN usage is essential to protect one’s communications and information especially when connected to a public Wi-Fi since this software creates secure tunnels to transfer information.
- Identity and Access Management (IAM) Software:
From the name given to this solution, we can understand that it is developed to identify and manage access given on a system. The process of authentication, authorization, and management of user identities this software includes ensures that only the individuals authorized have the right level of access to data.
- Security Information and Event Management (SIEM) Software:
This security software type is a combination of Security Information Management (SIM) and Security Event Management (SEM). This combination of systems offers an inclusive analysis of security incidents. This software enables real-time threat recognition, quick incident response, and compliance management.
- Patch Management Software:
The patch management software works on identifying, deploying, and verifying security patches to keep operating systems and applications up to date with latest available patches. Such software helps with the constant eliminating of threats even before attacking.
- Endpoint Security Software:
Endpoint security software works on protecting and securing endpoints or entry points of the organization’s devices such as computers, mobile devices, and servers. This solution will aid in detecting malware, phishing attacks, and many other threats using antivirus protection, firewalls, and device control.
- Web Application Firewalls (WAF):
This solution works on preventing attacks against the application level by filtering and monitoring HTTP traffic between a web application and the internet. It protects the application from threats like SQL injection, cross-site scripting, cross-site forgery, and file inclusion, among many others.
Conclusion
To conclude, implementing and integrating security software is essential to keep data and connections secure. Q-Pros Company helps create a defense line against evolving cyber threats and risks.

